1 Introduction
Accurate password strength measurement is crucial for securing authentication systems, but traditional meters fail to educate users. This paper introduces the first interpretable probabilistic password strength meter using deep learning to provide character-level security feedback.
2 Related Work & Background
2.1 Heuristic Password Meters
Early password strength meters relied on simple heuristics like LUDS (counting lowercase, uppercase, digits, symbols) or ad-hoc entropy definitions. These approaches are fundamentally flawed because they don't model actual password probability distributions and are vulnerable to gaming by users.
2.2 Probabilistic Password Models
More recent approaches use probabilistic models like Markov chains, neural networks, and PCFGs to estimate password probabilities. While more accurate, these models are black boxes that provide only opaque security scores without actionable feedback.
3 Methodology: Interpretable Probabilistic Meters
3.1 Mathematical Formulation
The core innovation is decomposing the joint probability of a password into character-level contributions. Given a password $P = c_1c_2...c_n$, the probability $Pr(P)$ is estimated using a neural probabilistic model. The security contribution of character $c_i$ is defined as:
$S(c_i) = -\log_2 Pr(c_i | c_1...c_{i-1})$
This measures the surprisal (information content) of each character given its context, providing a probabilistic interpretation of character strength.
3.2 Deep Learning Implementation
The authors implement this using a lightweight neural network architecture suitable for client-side operation. The model uses character embeddings and LSTM/Transformer layers to capture sequential dependencies while maintaining efficiency.
4 Experimental Results & Evaluation
4.1 Dataset & Training
Experiments were conducted on large password datasets (RockYou, LinkedIn breach). The model was trained to minimize negative log-likelihood while maintaining interpretability constraints.
4.2 Character-Level Feedback Visualization
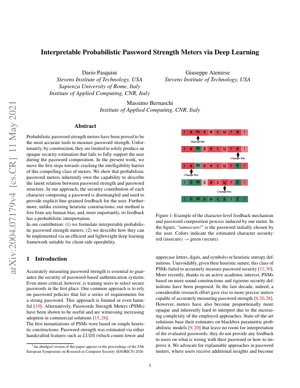
Figure 1 demonstrates the feedback mechanism: "iamsecure!" is initially weak (mostly red characters). As the user replaces characters based on suggestions ("i"→"i", "a"→"0", "s"→"$"), the password becomes stronger with more green characters.
4.3 Security vs. Usability Trade-off
The system demonstrates that users can achieve strong passwords with minimal changes (2-3 character substitutions) when guided by character-level feedback, significantly improving over random password generation or policy enforcement.
5 Analysis Framework & Case Study
Industry Analyst Perspective
Core Insight: This paper fundamentally shifts the paradigm from measuring password strength to teaching password strength. The real breakthrough isn't the neural architecture—it's recognizing that probabilistic models inherently contain the information needed for granular feedback, if only we ask the right questions. This aligns with the broader explainable AI (XAI) movement exemplified by works like Ribeiro et al.'s "Why Should I Trust You?" (2016), but applies it to a critically underserved domain: everyday user security.
Logical Flow: The argument progresses elegantly: (1) Current probabilistic meters are accurate but opaque black boxes; (2) The probability mass they estimate isn't monolithic—it can be decomposed along the sequence; (3) This decomposition maps directly to character-level security contributions; (4) These contributions can be visualized intuitively. The mathematical formulation $S(c_i) = -\log_2 Pr(c_i | context)$ is particularly elegant—it transforms a model's internal state into actionable intelligence.
Strengths & Flaws: The strength is undeniable: marrying accuracy with interpretability in a client-side package. Compared to heuristic meters that fail against adaptive attackers (as shown in Ur et al.'s 2012 SOUPS study), this approach maintains probabilistic rigor. However, the paper underplays a critical flaw: adversarial interpretability. If attackers understand what makes characters "green," they can game the system. The feedback mechanism might create new predictable patterns—the very problem it aims to solve. The authors mention training on large datasets, but as Bonneau's 2012 Cambridge study showed, password distributions evolve, and a static model might become a security liability.
Actionable Insights: Security teams should view this not just as a better meter, but as a training tool. Implement it in staging environments to educate users before production deployment. Combine it with breach databases (like HaveIBeenPwned) for dynamic feedback. Most importantly, treat the color-coding as a starting point—iterate based on how attackers adapt. The future isn't just interpretable meters, but adaptive interpretable meters that learn from attack patterns.
Example Analysis: Password "Secure123!"
Using the framework, we analyze a common password pattern:
- S: Moderate security (capital starting letter is common)
- ecure: Low security (common dictionary word)
- 123: Very low security (most common digit sequence)
- !: Low security (most common symbol position)
The system would suggest: replace "123" with random digits (e.g., "409") and move "!" to an unusual position, dramatically improving strength with minimal memorization burden.
6 Future Applications & Research Directions
- Real-time Adaptive Feedback: Meters that update suggestions based on emerging attack patterns
- Multi-factor Integration: Combining password feedback with behavioral biometrics
- Enterprise Deployment: Custom models trained on organization-specific password policies
- Password Manager Integration: Proactive suggestion systems within password managers
- Cross-lingual Adaptation: Models optimized for non-English password patterns
7 References
- Pasquini, D., Ateniese, G., & Bernaschi, M. (2021). Interpretable Probabilistic Password Strength Meters via Deep Learning. arXiv:2004.07179.
- Ribeiro, M. T., Singh, S., & Guestrin, C. (2016). "Why Should I Trust You?": Explaining the Predictions of Any Classifier. Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining.
- Ur, B., et al. (2012). How Does Your Password Measure Up? The Effect of Strength Meters on Password Creation. USENIX Security Symposium.
- Bonneau, J. (2012). The Science of Guessing: Analyzing an Anonymized Corpus of 70 Million Passwords. IEEE Symposium on Security and Privacy.
- Weir, M., et al. (2009). Password Cracking Using Probabilistic Context-Free Grammars. IEEE Symposium on Security and Privacy.
- Melicher, W., et al. (2016). Fast, Lean, and Accurate: Modeling Password Guessability Using Neural Networks. USENIX Security Symposium.